We at Komando.com do our best to keep you updated on all the online schemes, ploys and scams that are spreading around. Remember, scammers often rely on scare tactics, counting on you to overlook important details out of fear.
Take the notorious “sextortion” scam, for example. It’s an email that claims that someone has installed malware onto a porn site that you have visited and with some unknown “software magic,” they have video evidence of your “private” moments.”
It’s all fake, of course, and its just another good old blackmail/online extortion scheme that tries to scare you into ponying up your hard-earned cash to these cyberscammers.
And these past few months, the sextortion email scam has morphed into various forms. From a simple generic blackmailing scam, it has evolved into an ultra-personalized extortion attempt that’s even targeting companies and institutions.
Newer sextortion emails are even giving potential victims an ultimatum with subject lines like “Final warning, XXXXX. Pay up or else!”
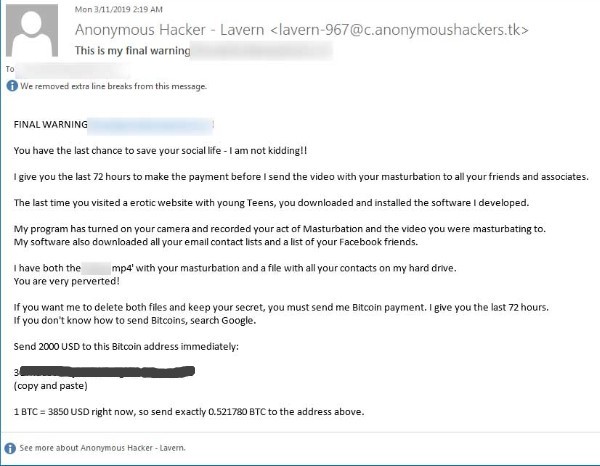
(Email courtesy Bleepingcomputer.com)
Of course, most of these sextortion emails are fake. Don’t be fooled by the inclusion of your full name, email address, passwords, phone number on the extortion email’s body, they are all there to make the attempt more compelling.
However, even though these emails are fake, hackers taking over your camera is a real possibility. Read on and see the difference between a fake sextortion threat and real spying done with malware.
Is remote spying a real threat?
Although this particular email threat is fake, remote access software, keyloggers and spying software are real.
In fact, webcam hacking is a real threat facing computer users every day. Believe me, you don’t want hackers taking over your webcam and watching your every move. That’s creepy!
Remote hackers can use malware dubbed RAT (Remote Access Trojan), to take over your computer completely, turn on your webcam without your knowledge and maliciously spy on you.
Hackers are reportedly even selling compromised webcams and archived webcam content for as low as $1. Worse yet, they could even turn off the webcam indicator light so you won’t even know if it has been turned on remotely. How’s that for scary, huh?
RAT malware could infect your computer via a number of ways. There is the usual “click on this link” method, distributed by email, text messaging and social media sites.
With this method, hackers will try and direct you to a website where the malicious software resides and from there, it will download and install to your computer as discreetly as possible.
Another method is if someone with physical access to your computer intentionally installs RAT software without your knowledge.
Remote access tools are a staple for troubleshooting and IT administrators everywhere, but if someone secretly installs these tools without your consent, then there might be more sinister ends at play.
How come they have your email, name, old passwords and phone numbers?
But how do these sextortion scammers manage to get your information in the first place?
As we said before, with the number of data breaches that are seemingly occurring every day, your email address, real name and even your old passwords are not that hard to acquire. These databases are typically available for sale on the dark web and even on public file sharing sites.
Remember, even if you do get a threatening email addressed to your name or with your old password and phone number attached, please don’t fall for it!
Note: To check if your information has been compromised, visit Have I Been Pwned. You can also try these new browser extensions that can check your credentials if they were involved in a past abuse.
Don’t pay the ransom!
If you receive any threatening email of this sort, please don’t give in by paying the bitcoin ransom!
A quick web search reveals that this extortion scam is getting popular lately. There may be variations in the words and the ransom amount but the M.O. is still the same – they claim to have video proof of your porn website excursions and they will release the video if you don’t pay the bitcoin amount.
In the words of Admiral Ackbar, “IT’S A TRAP!”
Note: With the number of data breaches that have occurred, real names and even your old passwords are not that hard to acquire either. Even if you do get a threatening email addressed to your name or with your old password attached, please don’t fall for it too!
But just in case…
If you want to be completely confident that your computer is free from spying malware, make sure you have some sort of anti-malware or anti-virus protection in place and do a deep scan.
As always, be wary of any web links that you encounter, even from trusted sources. Scrutinize links you receive very carefully and if you click through, never let websites trick you into installing software, usually disguised as “updates” or “video players.” Also, never open sketchy email attachments from anyone, even contacts that you trust.
There are free third-party anti-virus tools online that will aid you in checking and removing malware, spyware and virus infections. Malwarebytes, for instance, is a proven malware removal tool for both Macs and PCs.
Windows 10 also has a free malware detection and extraction program called the Microsoft Windows Malicious Software Removal Tool. Introduced way back in Windows Vista, this tool runs in the background, quietly scanning your system and will alert you if it detects any suspicious activity.
Some types of malware can be stealthy and persistent even after a scan, though. In this case, you can try troubleshooting your PC in Safe Mode or use a diagnostic boot CD or USB portable drive to track down any pesky viruses.
Have a question about email scams or anything tech-related? Kim has your answer! Click here to send Kim a question, she may use it and answer it on her radio show.

