There’s no doubt in anybody’s mind that phishing scams are on the rise. But as more people become aware of the tactics these scammers are using, the scams themselves become more complicated and harder to detect.
For a perfect example, look no further than the sheer volume of COVID-19 and stimulus scams circulating the web right now. These topical subjects make great bait for victims, and unless you’re paying close attention, it’s easy to get tricked into signing away your personal data. Tap or click here to see how to avoid COVID-19 phishing scams.
But timely subject matter isn’t the only thing to watch out for from scammers these days. A horrific new banking scam has been found that targets customers with an extremely convincing fake login screen. It’s one of the most sophisticated campaigns in recent memory, and if you’re not careful, it might ensnare you too. Here’s what to look out for.
Bank of America customers targeted by sophisticated phishing campaign
According to security researchers at Armorblox, Bank of America customers are at high risk of being targeted by a wide-sweeping phishing campaign with an assortment of highly-convincing emails, websites and login pages.
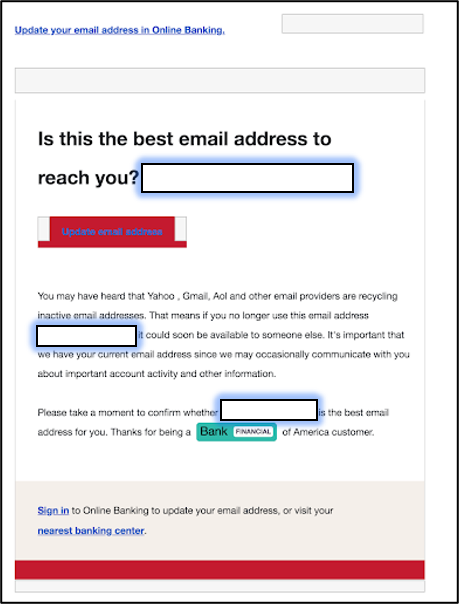
The first sign of the scam is a realistic-looking email purporting to be from Bank of America itself. Designed to look like a run-of-the-mill “update your contact information” message, the email is painstakingly constructed to look as authentic as possible.
If you follow the link from the message, you’re greeted with what appears to be a normal Bank of America login page. This is where the crux of the scam takes place. If you enter your email address and password, this information is siphoned up by the website and sent back to the scammers responsible.
What’s more, it even asks for your security questions to further doom your account to compromise.
What’s most concerning is how this message was able to get past some of the more robust spam filters available on the web. The campaign is not a mass-mailer like many of the more common ones making the rounds, but a targeted “spear-phishing” campaign with a more limited scope.
How can I spot this campaign and other phishing schemes?
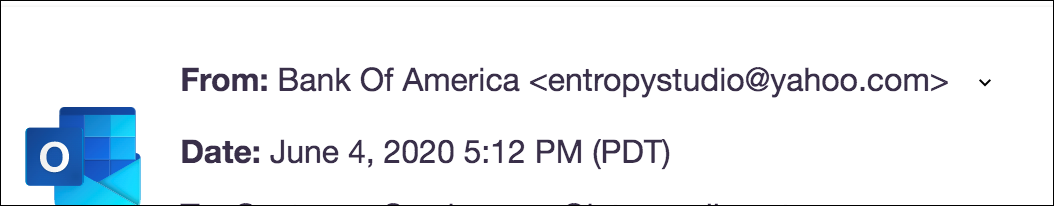
As tricky as this Bank of America scam is to decipher, there are a few key aspects to the campaign that makes the whole thing fall apart if noticed. The first, and most obvious, is the domain name of the email sender.
As you can see, the domain name is an ordinary Yahoo email address. Were this an actual email from Bank of America, the domain would say as much.
But this obvious misstep isn’t only seen in the email itself. If you make the mistake of opening the fake login page, you can also look at the URL to determine its fraudulent nature.
The domain, in this case, is “nulledco.store,” which is obviously unrelated to Bank of America. A quick glance at the URL or sender field in this email account is enough to bring the entire narrative down.
In a spot of good news, you can use this same trick to identify other phishing attempts on your account, as it’s quite difficult for hackers to hijack an official company email address for mass-mailing campaigns. The same can be said with phishing websites.
Attack vectors like magecart attacks are far more dangerous, as they embed themselves into existing webpages with trusted URLs. Tap or click here to see what a successful magecart attack can do.
If you want to avoid getting scooped up into a phishing campaign, here are some easy steps you can take to stay safe:
- Refrain from opening emails if you don’t know the sender. This bears repeating, as it’s one of the easiest ways to avoid getting suckered into a phishing campaign. If you never open the malicious message, it cannot hurt you.
- Never download attachments unless you’re 100% sure of the contents. Even if an email comes from a trusted friend or relative, it’s worth giving them a phone call to make sure the attachment was actually sent by them. Email attachments are one of the most common vectors for malware installation, after all.
- Always check the sender’s email domain. If the email claims to come from a trusted source, use your best judgment and look at the sender field. If it’s from a mismatched URL, that’s as big of a red flag for phishing as any.
- Don’t click unknown links in emails. Just like with attachments, it’s worth getting in touch with the email’s sender to make sure you’re not visiting any malicious or dangerous websites.
- Check the URL for any site you visit. You can do this by hovering your cursor over a link before clicking on it. This doesn’t just apply to links from emails, but anywhere else you visit on the web. If a URL appears mismatched to the contents of the page, get as far away as you can.
- If an email or website asks for personal data or login information, ignore it. Most businesses and platforms will never ask for your information point-blank, and will usually give you the option to reset these things yourself.
If you follow these steps, there isn’t much a phishing campaign can do to you other than try again. But who knows, maybe these scammers will change up their tricks again as more people catch on to their nonsense.