Phishing is a common cyberattack that everyone should know about. It’s a simple premise, usually performed through email. The malicious actors send messages pretending to be from trusted sources such as delivery services, banks and just about any well-known company.
Crooks send countless messages and wait for potential victims to bite. The goal is to steal sensitive data such as credit card and login information or to install malware on a victim’s device. Tap or click here to find out which company is impersonated in nearly half of all phishing attacks globally.
Now, a LinkedIn tool is being used in phishing attacks. This is awful news since so many people use the site to find jobs or recruit employees. Here’s how the scam works and what to look out for.
Here’s the backstory
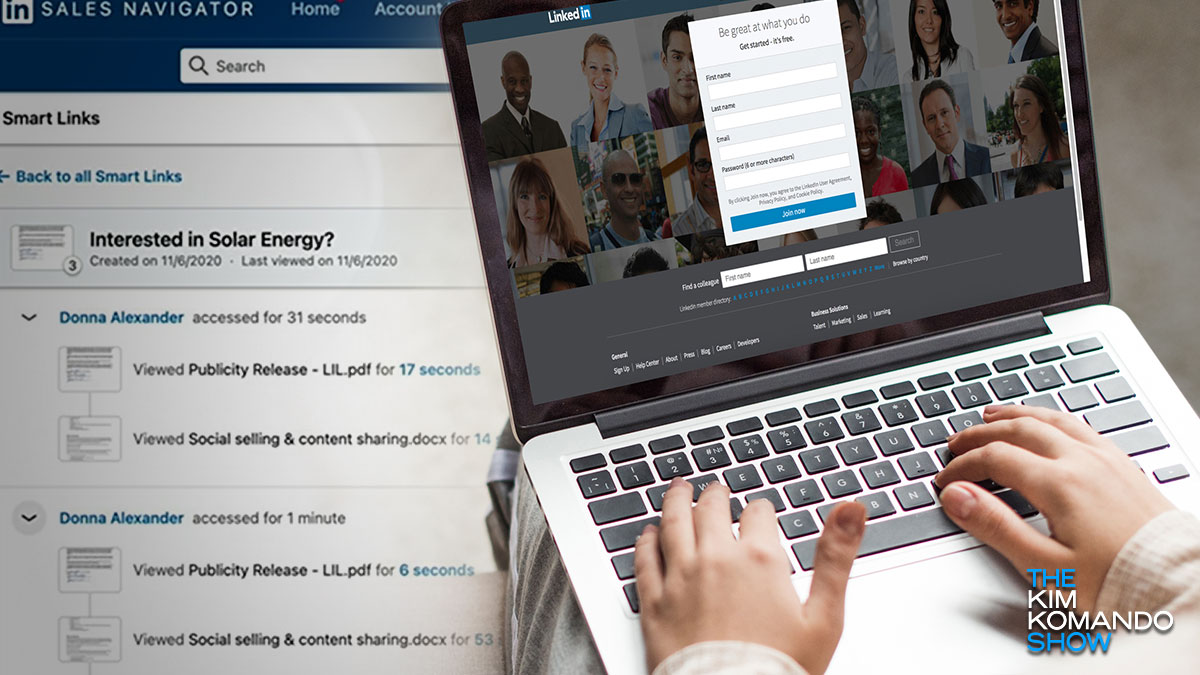
Premium LinkedIn accounts like Enterprise and Sales Navigator use the Smart Link tool, making it easier to package and share content. With Smart Link, a company can bundle up to 15 assets, such as PDFs, case studies, links, brochures, and presentations to send via email. The recipient receives a single Smart Link that leads to the entire bundle.
Unlike a landing page which would require visitors to fill in a form with their information, Smart Links immediately capture their LinkedIn information. It’s a valuable tool for tracking who clicked through the assets and how long they stayed. Unfortunately, this also leaves room for abuse.
Crooks using LinkedIn’s Smart Link
Cybercriminals are using LinkedIn’s Smart Link to bypass secure email gateways (SEGs), designed to prevent unwanted emails such as spam, phishing attacks and malware from reaching your inbox.
Cybersecurity company Cofense spotted threat actors impersonating the Slovakian Postal Service to inform potential victims that they need to pay a fee for a pending shipment. The address, subject line and message seem legitimate, complete with bogus reference numbers.
By using Smart Link, the crook bypasses many protection tools that would typically block the message or URL contained within it.
When the recipient clicks the confirm button, they’re directed to a page where they’re asked to enter their credit card information to pay for the shipment waiting for them. The fee isn’t high (about $5), but the point here is to steal the victim’s payment credentials.
Victims are then sent a text message with a phony confirmation code to enter into the next page. It doesn’t matter what numbers they put in — they’re taken to a final confirmation page to complete the scam.
Using Smart Link also gives cybercriminals insights into how well their malicious campaigns work. They can then make adjustments to snare more victims.
Cofense says that the phishing page is still up and running. Even though this campaign targeted Slovakians, there are others like it right here. For example, scammers impersonate the United States Postal Service to steal personal and financial information. Tap or click here for tips on avoiding this dangerous scheme.
Protect yourself from phishing scams
BleepingComputer requested comment on the scam, and LinkedIn responded by saying that it’s working to take action against crooks who use LinkedIn as part of their phishing campaigns. The company encourages its members to use two-factor authentication and report suspicious activity.
LinkedIn’s Help Center has more information for spotting scams involving impersonators.
Here are some more online safety tips:
- Safeguard your information — Never give out personal data if you don’t know the sender of a text or email or can’t verify their identity. Criminals only need your name, email address and telephone number to rip you off.
- Always use 2FA — Use two-factor authentication (2FA) for better security whenever available. Tap or click here for details on 2FA.
- Avoid links and attachments — Don’t click on links or attachments you receive in unsolicited emails. They could be malicious, infect your device with malware and/or steal sensitive information.
- Beware of phishing emails — Scammers piggyback on breaches by sending malicious emails to trick you into clicking their links that supposedly have important information. Look out for strange URLs, return addresses and spelling/grammar errors.
- Use strong, unique passwords — Tap or click here for an easy way to follow this step with password managers.
- Antivirus is vital — Always have a trusted antivirus program updated and running on all your devices. We recommend our sponsor, TotalAV. Right now, get an annual plan with TotalAV for only $19 at ProtectWithKim.com. That’s over 85% off the regular price!
LinkedIn is a valuable tool for recruiters
Small businesses have unique needs, and it’s more important than ever to have the right people on your team. That’s why Kim trusts our sponsor, LinkedIn Jobs, to help. LinkedIn Jobs matches your open role with qualified candidates and puts your post in front of members daily so you can hire the right person faster.
Find the perfect fit for your business with LinkedIn Jobs. And, for a limited time, post a job for free — just visit LinkedIn.com/kim to get started today!
Keep reading
Watch out for the nine most creative scams from Kim’s inbox — they’re scarily deceptive
Use Microsoft OneDrive? Here’s a phishing attack you need to know about