Take a moment to think about all the private data stored on your computer. You probably have all your photos, videos, resumes, contacts, documents and other sensitive information saved on your PC or Mac. Someone could do a lot of damage with that information, which is why it’s important to know how to spot computer spies.
You may not know this, but your work computer probably has spyware on it. Employers often install bossware onto work devices, which lets them see every keystroke you make. Here’s all you need to know about the secret software watching your every move at work.
There’s not much you can do to stop your boss, but good news: There’s a lot you can do to stop criminals from accessing your computer. In this guide, you’ll learn some simple strategies you can use to make sure no one is spying on your computer. Just know that the exact steps may vary depending on your device.
1. Check your PC’s recent items
So someone’s been poking around your computer, opening your files and applications left and right, there’s bound to be traces of it, right? Correct. On both PCs and Macs, there are quick and easy ways to view recently accessed files, folders and even applications.
With these tools, if you notice an item that you don’t remember opening, then that’s a sure sign that an unauthorized party has been accessing your system without your knowledge. Here’s how you view your recent items on both PCs and Macs:
On PC:
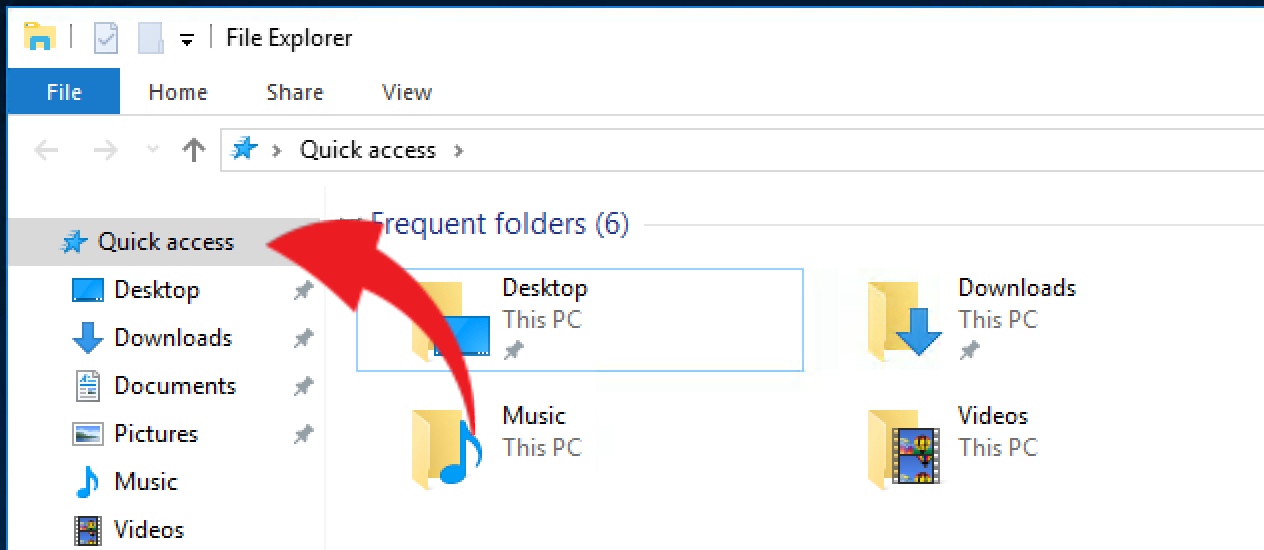
Recent Files:
- Open a File Explorer window by clicking its taskbar shortcut, opening the Documents folder or by pressing Windows key + E.
- At the left side of the File Explorer’s menu, click “Quick Access.” This will show a list of files that were recently opened. If you see something in this list that you don’t remember opening, then someone may have been poking around your computer.
On Mac:
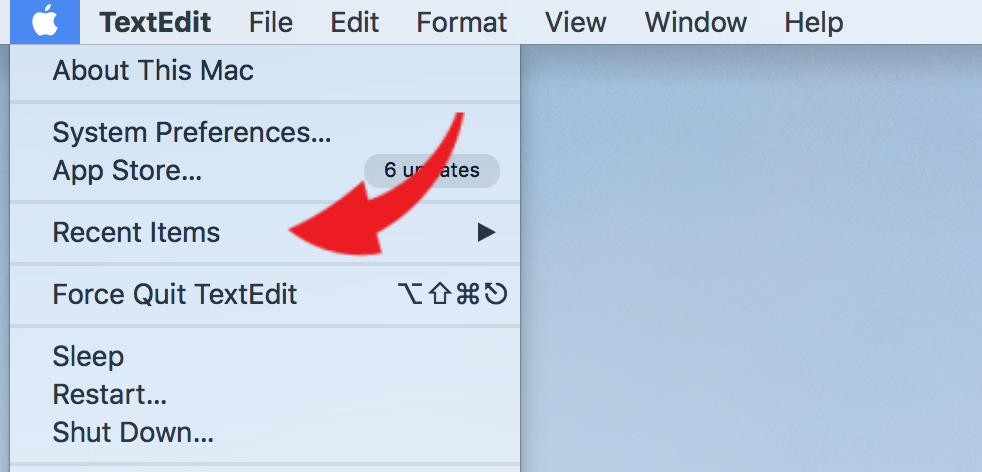


Recent items:
- Click on the Apple logo on the left-hand side of the menu bar.
- Hover your mouse over “Recent Items”
- Here, you’ll see the 10 most recent items accessed in three categories: Applications, Documents and Servers
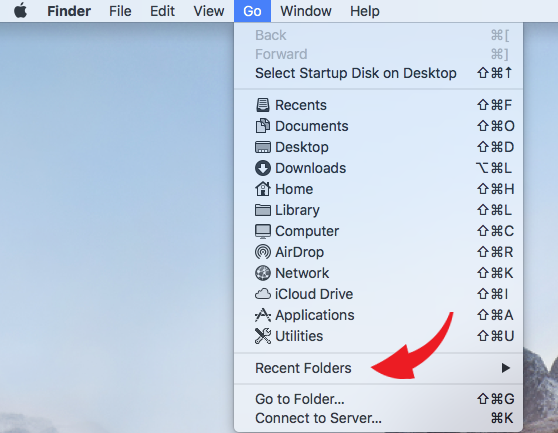


Recent folders:
- Open a Finder window
- While the window is active, click “Go” on the menu bar
- Hover your mouse over “Recent Folders.” Similar to “Recent Items,” you’ll see the 10 folders that were most recently accessed
BONUS TIP: This free tool shows you what someone has searched for using Google, Yahoo, Facebook and more
2. Check your web browser’s history
Another good area to check for unauthorized access is browsing activity. Although a savvy user can always use a web browser’s Incognito or Private mode or delete their browsing histories, it doesn’t hurt to review web browsing activity for snoops.
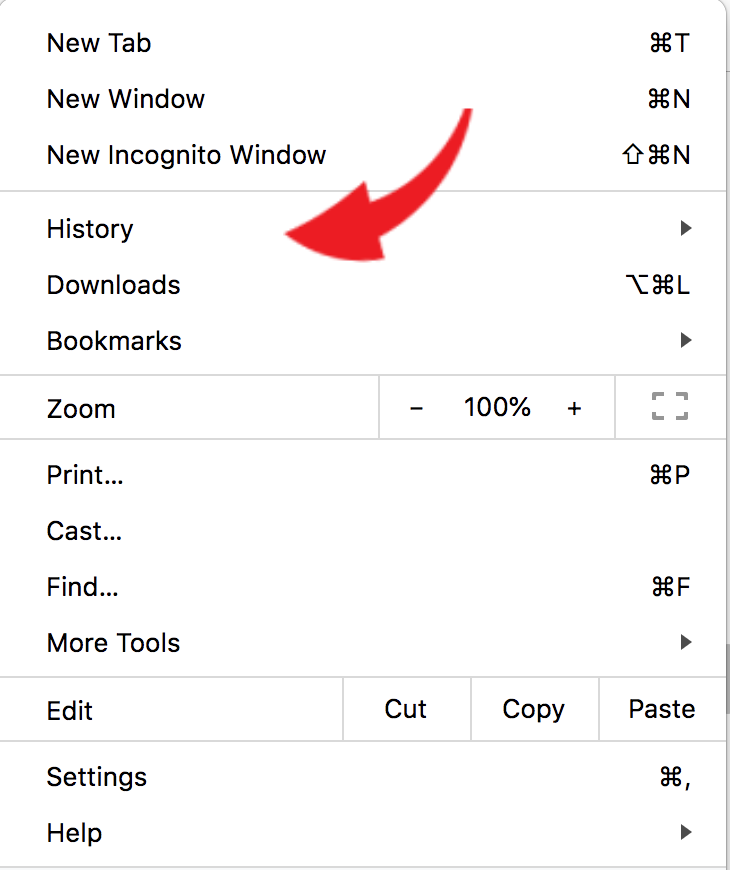
Google Chrome
- Click the three vertical dots on the upper-right side of your Chrome window.
- Hover on “History.”


Mozilla Firefox:
- Click the “View history, saved bookmarks and more” icon on the menu bar (it looks like a row of books).
- Click on “History.”


Microsoft Edge:
- Click the “Hub” icon (it looks like a speeding star).
- Click on “History.”


Safari:
- Open Safari
- On the Apple menu bar, click “History >> Show All History.”


WANT MORE? Here are 7 essential browser tricks every computer user needs to know
If you’re still wondering how to spot computer spies, here’s another nifty trick.
3. Review your computer’s Logon Events
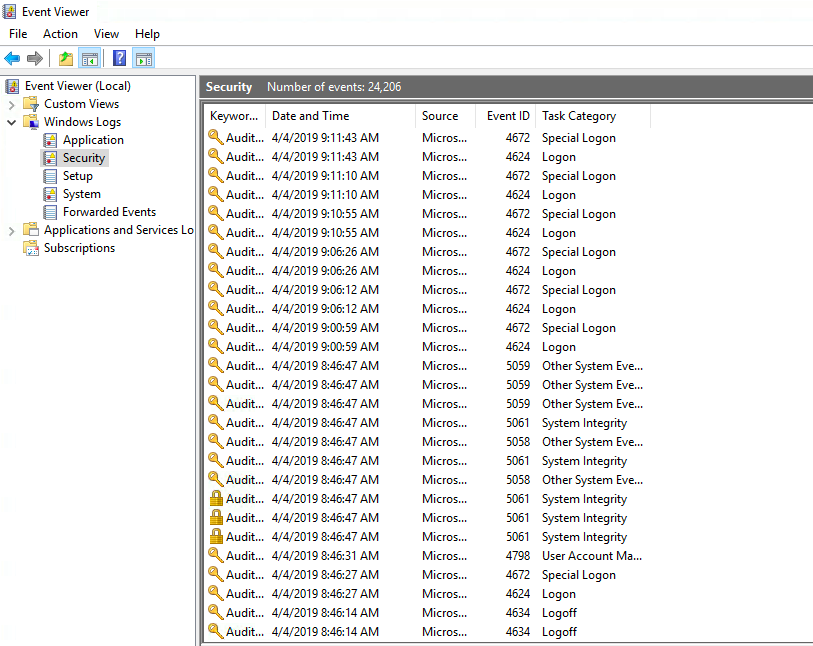
To see all the login activities on your PC, use Windows Event Viewer. This tool will show you all Windows services that have been accessed, as well as logins, errors and warnings.
To access the Windows Event Viewer, go to Control Panel >> System and Security >> Administrative Tools >> Event Viewer.
An easier way to access the Event Viewer is to simply press the Windows + R keys. Type “eventvwr” in the “Run” dialog box. This will open the Event Viewer.
Now on the left pane, click on an item called Security.
This will show you a list of all the login events on your PC. Under the Event ID column, look for the number 4624 for standard logons, 4672 for administrative logons and 4634 for logoffs. Click the entry for additional details and check if another user has logged in to your system while you’re away.


On Macs, you can use the Console tool to check if someone attempted to wake your computer while it’s locked or in sleep mode.
To access this tool, use Spotlight Search (Command + Space) then look for the word “Console” and then press Enter. On the Console window, click “All Messages” then on the Search field (upper-right side of the window), type “wake” to see all the relevant events and their timestamps.
BONUS TIP: 16 Windows 10 tricks you’ll wish you knew sooner
4. Now that you know how to spot computer spies, here’s how to kick them out
Locking your computer and using a strong password to log back in are two of the most basic computer security essentials we are always advised to do.
In office spaces, the lock screen is a convenient feature that suspends your activities and protects your work from would-be visual snoopers without completely shutting your computer down.
Always lock your computer when you’re away so would-be snoopers can’t access it. On Windows, you can use the shortcut Windows key + L to quickly lock your PC.
On a Mac, you can use the shortcut Control + Shift + Eject (Control + Shift + Power button on Macs without disk drives) or Control + Command + Q to quickly lock it. You can also click on the Apple logo on the menu bar and select Lock Screen.
Note: Make sure you set your Mac’s security options to require the password immediately after it’s locked. You can set this by opening System Preferences >> Security & Privacy.
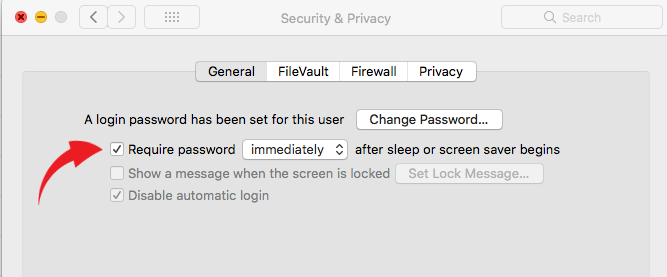


While you’re at it, make sure you have a strong password for your account. When it’s your own computer, you might be in the habit of using a simple password so you can log in faster. That’s why many people use weak passwords like “password” or “123456,” Bad idea. Hackers can guess an easy password in minutes.
That’s why you need to get into the habit of creating unique, complex passwords. These take more time to create, but they keep your information safe. Of course, you also need a good way to remember them.
RELATED: Here are the worst passwords you should stop using now
5. How about keyloggers?
Did you know that there are programs that exist solely to capture information coming from your keyboard? They’re called keystroke loggers, or keyloggers for short, and they can be nasty hacker tools to steal your information.
While companies and parents can use keyloggers for legal monitoring, a scammer could use one to invade your privacy or steal your identity. They come in software and hardware form and are not something to take lightly.
Physical keyloggers are easy to hide inside computers. They can also sit on wires and cables, and if you don’t know exactly what you’re looking for, you can easily miss it. Fortunately, these external keyloggers are limited in what they can do.
Unfortunately, the software counterparts are just as hard to detect and can do a lot more damage. Of course, many of your programs create logs, so you’ll have to do some investigating. Look for programs you don’t recognize and research them using Google.
If you do find a keylogger, you will need to manually remove it. You can try security programs, but keyloggers are designed to avoid these. If you liked this guide on how to spot computer spies, tap or click here to sniff out keyloggers on your device.

